Abstract:
In an era of escalating cyber threats and stringent regulatory demands, effective vulnerability management is non-negotiable. The Common Vulnerability Scoring System (CVSS) offers a global standard, but its implementation often fragments across disconnected spreadsheets, hindering true risk-informed decision-making and auditable compliance. This whitepaper outlines how Siemens Polarion ALM, supercharged by Nextedy RISKSHEET, transforms CVSS from a mere scoring exercise into an integrated, actionable, and transparent component of your cybersecurity and product development lifecycle. We will explore how this synergy provides a single source of truth, empowers teams with executable control measures, enforces granular data access, and leverages reusable knowledge catalogs, ultimately enabling organizations to manage cybersecurity risks with unprecedented efficiency and confidence.
The Escalating Challenge of Vulnerability Management
Modern products and systems are increasingly complex and interconnected, expanding the attack surface for cyber threats. For organizations, especially in regulated industries (e.g., automotive, medical devices, critical infrastructure), the challenges are manifold:
- Disconnected Tools & Data Silos: CVSS assessments, risk registers, and mitigation plans often live in disparate spreadsheets or niche tools, leading to a fragmented view of the risk landscape.
- Manual, Error-Prone Processes: Manual data entry, score calculation, and linking risks to mitigations are inefficient and susceptible to human error.
- Lack of Actionable Intelligence: Static risk scores without clear links to executable mitigation tasks delay remediation and obscure accountability.
- Audit & Compliance Burdens: Demonstrating consistent application of CVSS, traceability from vulnerability to mitigation, and controlled access to sensitive data can be an overwhelming audit challenge.
- Inefficient Resource Allocation: Without a clear, contextualized view of vulnerabilities, prioritizing remediation efforts becomes a guessing game.
Introducing CVSS: A Common Language for Vulnerability Severity
The Common Vulnerability Scoring System (CVSS) provides an open and standardized method for rating the severity of IT vulnerabilities. It assigns a numerical score (0-10) based on:
- Base Metrics: Intrinsic characteristics of a vulnerability (e.g., Attack Vector, Impact on Confidentiality, Integrity, Availability).
- Temporal Metrics: Factors that change over time (e.g., Exploit Code Maturity, Remediation Level).
- Environmental Metrics: Vulnerability aspects specific to an organization’s environment (e.g., Modified Impact based on security controls in place, Security Requirements).
CVSS enables organizations to prioritize responses and resources according to threat severity, fostering a common understanding among security professionals, IT managers, and vendors.
The Polarion + Nextedy RISKSHEET Advantage: Transforming CVSS into an Integrated Discipline
Simply adopting CVSS isn’t enough; its power is unlocked when deeply integrated into the Application Lifecycle Management (ALM) and risk management fabric. This is where the synergy of Siemens Polarion ALM and Nextedy RISKSHEET delivers transformative value:
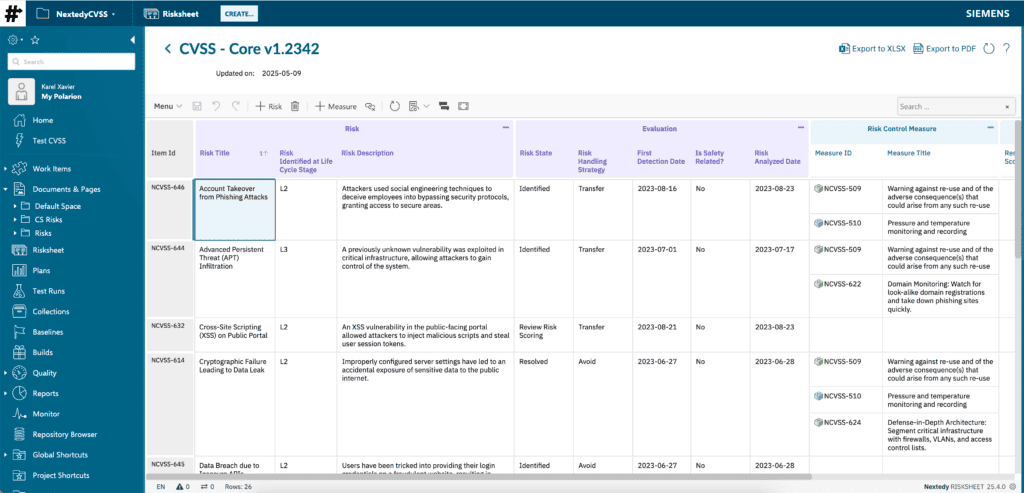
- Unified Platform – Single Source of Truth:
- Why it matters: Eliminates data silos. Cybersecurity Risk work items (representing CVSS assessments) reside within Polarion, alongside requirements, design specifications, test cases, and other project artifacts.
- Nextedy RISKSHEET: Provides an intuitive, Excel-like interface directly within Polarion to manage these Risk items, making complex data easily accessible and editable without leaving the ALM environment.
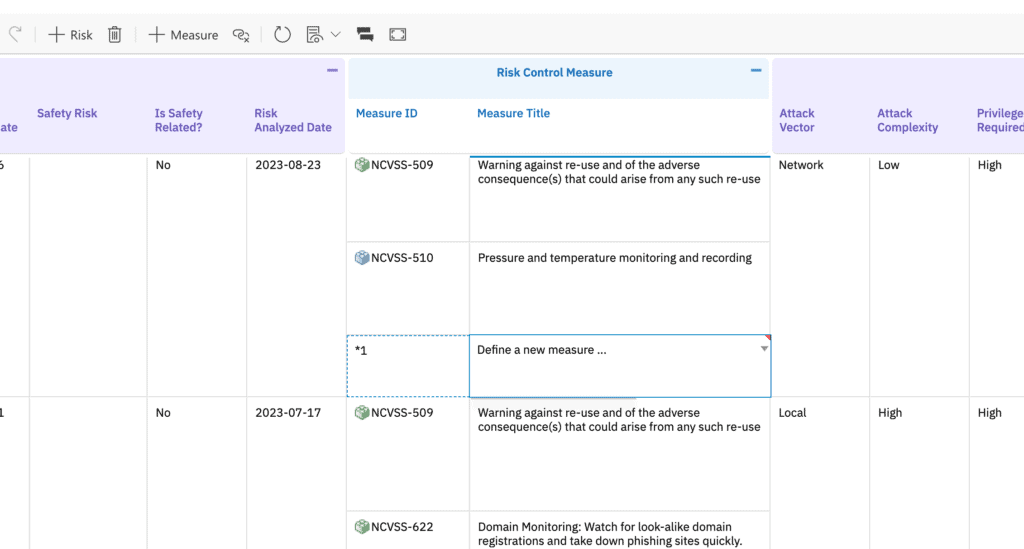
- Actionable Intelligence – Executable Control Measures:
- Why it matters: Moves beyond passive risk logging. Mitigations are not just descriptive text.
- Nextedy RISKSHEET & Polarion: Control Measures (displayed in columns like “Measure ID” and “Measure Title” within RISKSHEET) are defined as executable Polarion Work Items (e.g., types such as Software Risk Control Measures or System Risk Control Measures). These are linked via a “mitigates” relationship. This means each mitigation has an owner, status, due date, and can be tracked through development and verification workflows like any other task or requirement.
- Controlled Visibility – Granular Permissions:
- Why it matters: Protects sensitive cybersecurity intelligence. Not all team members need access to detailed attack vectors or specific vulnerability exploitation details.
- Polarion’s Robust Permissions Model: Governs who can view or edit specific fields within a Cybersecurity Risk work item (e.g., the “Attack Vector” field, or “Threat Description”). Nextedy RISKSHEET inherently respects and operates within these Polarion permissions, ensuring that sensitive information is only accessible to authorized personnel, crucial for maintaining security integrity and compliance.
- Structured Knowledge – Reusable Catalogs:
- Why it matters: Leverages existing knowledge and ensures consistency. Avoids re-inventing the wheel for common threats or system components.
- Polarion Work Items as Catalogs: Information displayed in columns like “Threat Model Diagram” within RISKSHEET are not just string fields; they represent links to distinct Threat Model work items in Polarion. This allows for the creation and maintenance of reusable catalogs of threat diagrams, assets, or even common vulnerability patterns, which can be consistently referenced across multiple Cybersecurity Risk assessments.
- Efficiency & Accuracy – Automation and Intuitive Interface:
- Why it matters: Reduces manual effort, minimizes errors, and accelerates the assessment process.
- Nextedy RISKSHEET: Automates all CVSS score calculations (Base, Temporal, Environmental, Resulting Score, and the CVSS Vector String) in real-time as metric values are selected. Its spreadsheet-like interface drastically reduces the learning curve and makes data entry straightforward.
- End-to-End Traceability & Auditability:
- Why it matters: Simplifies compliance and provides a clear audit trail for every vulnerability.
- Polarion’s Core Strength: Every Cybersecurity Risk item, its associated metrics, linked control measures, and any changes are versioned and auditable. This provides an irrefutable record for regulatory bodies and internal reviews.
A Glimpse into the CVSS Workflow with Polarion and Nextedy RISKSHEET
While not a step-by-step manual, understanding the flow highlights the integrated nature:
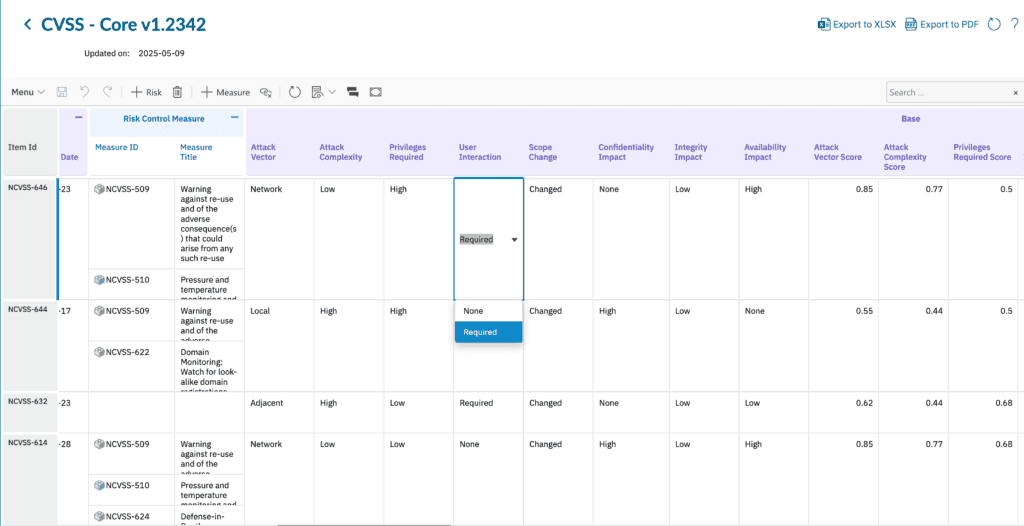
- Phase 1: Risk Identification & CVSS Base Metric Assessment
- Cybersecurity risks are documented as dedicated Risk work items within the RISKSHEET view.
- Essential details like “Risk Title,” “Risk Description,” “Origin” (potentially from a catalog of system components), and links to “Connected Feature”s or “Threat Model Diagram”s are captured.
- Users select CVSS Base Metrics (e.g., from dropdowns for “Attack Vector,” “Confidentiality Impact,” “Privileges Required”) from predefined, validated lists (Polarion enumerations).
- RISKSHEET instantly calculates individual metric scores and the overall “Base Score.”
- Phase 2: Contextualization, Mitigation & Final Scoring
- Temporal Metrics (e.g., “Exploit Code Maturity,” “Remediation Level”) are added to reflect the current threat landscape.
- Environmental Metrics (e.g., “Modified Attack Vector,” and security requirements like “Confidentiality Requirement”) tailor the assessment to the specific operational context.
- Crucially, Control Measures are identified and linked. These are actionable Software Risk Control Measure or System Risk Control Measure work items, assigned to teams for implementation and verification, visible through columns like “Measure ID” and “Measure Title.”
- RISKSHEET dynamically recalculates scores, culminating in the “Environmental Score” (or “Temporal Score” if environmental metrics are not used), the final “Resulting Score,” the comprehensive “CVSS String,” and a clear “Risk Severity” rating.
- The “Risk Handling Strategy” (e.g., Mitigate, Accept) and its “Risk Handling Strategy Justification” are documented, alongside approval workflows (e.g., “Exception Approval Status,” “Exception Approved by”).
Key Differentiators for Cybersecurity Leaders & Architects:
- Mitigation as Managed Work: Control Measures are not static entries but fully managed Polarion tasks or requirements, integrated into sprints, backlogs, and verification processes. This ensures accountability and follow-through.
- Secure Collaboration: Polarion’s permissions, enforced by RISKSHEET, allow diverse teams to collaborate on risk assessment while protecting sensitive details like attack vectors or unpatched vulnerability specifics from unauthorized access.
- Leveraging Enterprise Knowledge: The ability to link to reusable work item catalogs (e.g., Threat Model work items, pre-defined Feature components) promotes consistency and efficiency, building a cumulative cybersecurity knowledge base within Polarion.
- Seamless ALM Integration: CVSS assessment isn’t an isolated activity. It’s woven into the fabric of requirements engineering, software development, testing, and release management, ensuring security is considered at every stage.
Terminology Mapping: Bridging CVSS Concepts with Polarion & RISKSHEET
| CVSS Concept | Column in RISKSHEET (Header/Label) | Polarion Equivalent (Cybersecurity Risk Work Item) |
| Risk / Vulnerability ID | Item ID (Implicit) | Work Item ID (e.g., NCVSS-646) |
| Risk Title | Risk Title | “Title” field |
| Risk Description | Risk Description | “Description” field (rich text) |
| Base Metrics & Scores | ||
| Attack Vector | Attack Vector | “Attack Vector” field (using Attack Vector enumeration) |
| Attack Complexity | Attack Complexity | “Attack Complexity” field (using Attack Complexity enumeration) |
| Privileges Required | Privileges Required | “Privileges Required” field (using Privileges Required enumeration) |
| User Interaction | User Interaction | “User Interaction” field (using User Interaction enumeration) |
| Scope | Scope Change | “Scope Change” field (using Scope Change enumeration) |
| Confidentiality Impact | Confidentiality Impact | “Confidentiality Impact” field (using Confidentiality Impact enumeration) |
| Integrity Impact | Integrity Impact | “Integrity Impact” field (using Integrity Impact enumeration) |
| Availability Impact | Availability Impact | “Availability Impact” field (using Availability Impact enumeration) |
| Base Score | Base Score | “Base Score” field (float, formula-calculated) |
| Temporal Metrics & Scores | ||
| Exploit Code Maturity | Exploit Code Maturity | “Exploit Code Maturity” field (using Exploit Code Maturity enumeration) |
| Remediation Level | Remediation Level | “Remediation Level” field (using Remediation Level enumeration) |
| Report Confidence | Report Confidence | “Report Confidence” field (using Report Confidence enumeration) |
| Temporal Score | Temporal Score | “Temporal Score” field (float, formula-calculated) |
| Environmental Metrics & Scores | ||
| Modified Attack Vector (Example) | Modified Attack Vector | “Modified Attack Vector” field (using corresponding enumeration) |
| Confidentiality Requirement (Ex.) | Confidentiality Requirement | “Confidentiality Requirement” field (using corresponding enumeration) |
| Environmental Score | Environmental Score | “Environmental Score” field (float, formula-calculated) |
| Resulting Scores & Mitigation | ||
| Resulting (Final) Score | Resulting Score | “Resulting Score” field (float, formula-calculated) |
| CVSS Vector String | CVSS String | “CVSS String” field (string, formula-calculated) |
| Severity | Risk Severity | “Severity” field (using CVSS Severity enumeration, formula-calculated) |
| Risk Handling Strategy | Risk Handling Strategy | “Risk Handling Strategy” field (using Handling Strategy enumeration) |
| Mitigation / Control Measure | Measure ID, Measure Title | Link (e.g., “mitigates” role) to a Control Measure work item type |
| Linked Threat Model | Threat Model Diagram | Link (e.g., “relates to” role) to a Threat Model work item type |
Conclusion: Elevating CVSS to a Strategic Imperative
For cybersecurity leaders, discipline owners, and Polarion solution architects, the combination of Polarion ALM and Nextedy RISKSHEET elevates CVSS vulnerability management from a tactical chore to a strategic, integrated discipline. It provides the visibility, control, and efficiency needed to proactively manage cyber risks, ensure compliance, and build more secure products. By centralizing data, automating complex calculations, enabling secure collaboration with actionable mitigations, and leveraging reusable knowledge, this solution empowers organizations to not just score vulnerabilities, but to effectively neutralize them within their existing development ecosystem.
To witness how Nextedy RISKSHEET can revolutionize your CVSS process within Polarion and to discuss your specific cybersecurity risk management challenges, contact info@nextedy.com or request a personalized demonstration.