Master Cybersecurity Risk.
Secure Your Products.
Inside Polarion.
Secure Your Products.
Inside Polarion.
Unify TARA, CVSS, STRIDE, and other cybersecurity risk assessments with complete traceability and enterprise-wide control. Achieve compliance with IEC 62443, ISO/SAE 21434, and industry best practices – efficiently and reliably with Nextedy RISKSHEET.
Try Nextedy Cybersecurity Solution Online
You’re about to experience our Nextedy Cybersecurity STRIDE demo.
Just fill out the form and get instant access to the Demo Environment.Looking for TARA or CVSS instead? You can choose them here: 👉 nextedy.com/try-online
“Nextedy has truly exceeded our expectations with their exceptional service and innovative software solutions. “
Senior Manager
Advanced R&D-Digital Tooling

❌ Cyber Risks & Requirements: Out of Sync.
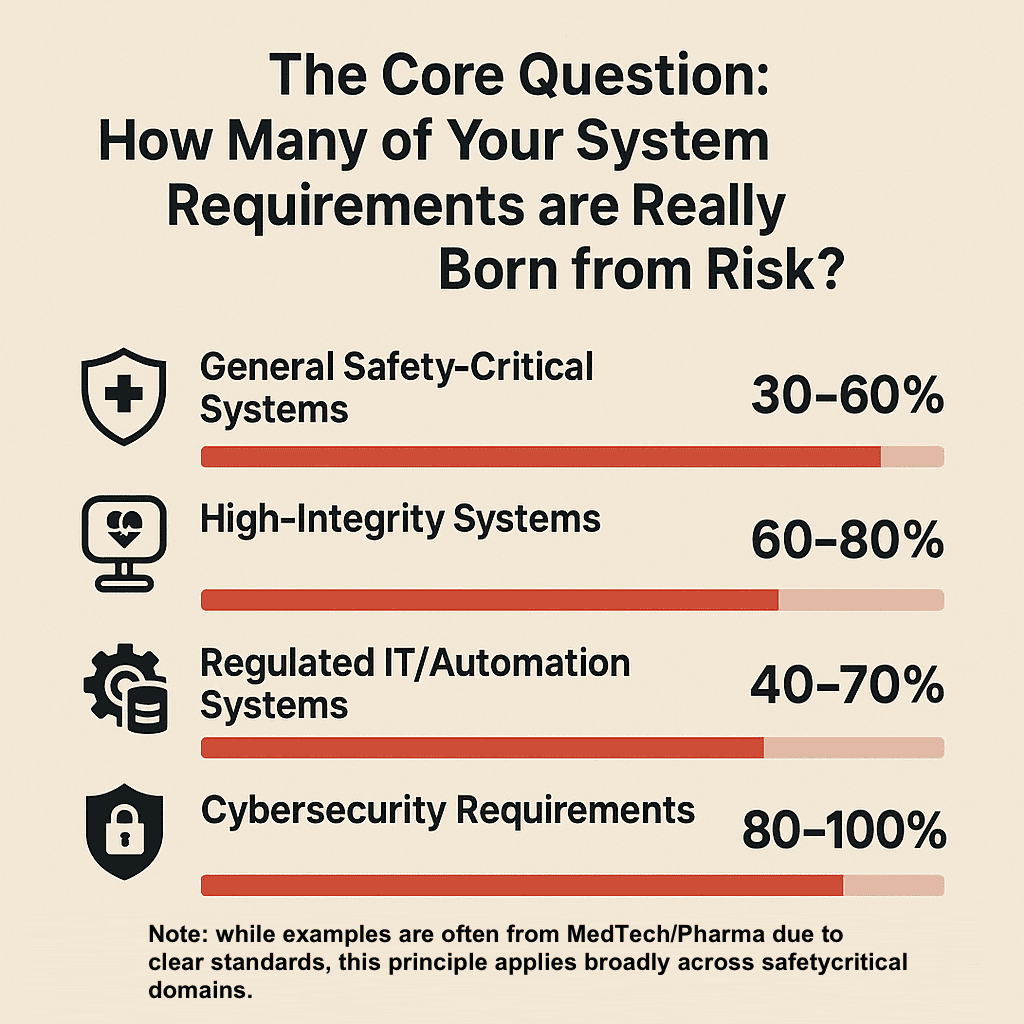
- 60–80% of requirements come from safety & cyber risk analyses (HARA/FMEA, TARA/CVSS/STRIDE), yet they live in separate spreadsheets, disconnected from requirements.
- Risk, requirements, and verification drift apart; traceability becomes manual; audits turn into fire drills.
SOLUTION
✅ One Living Risk Model in Polarion with Nextedy RISKSHEET
Centralize safety & cyber risks, calculations, and links in Polarion—live and auditable.
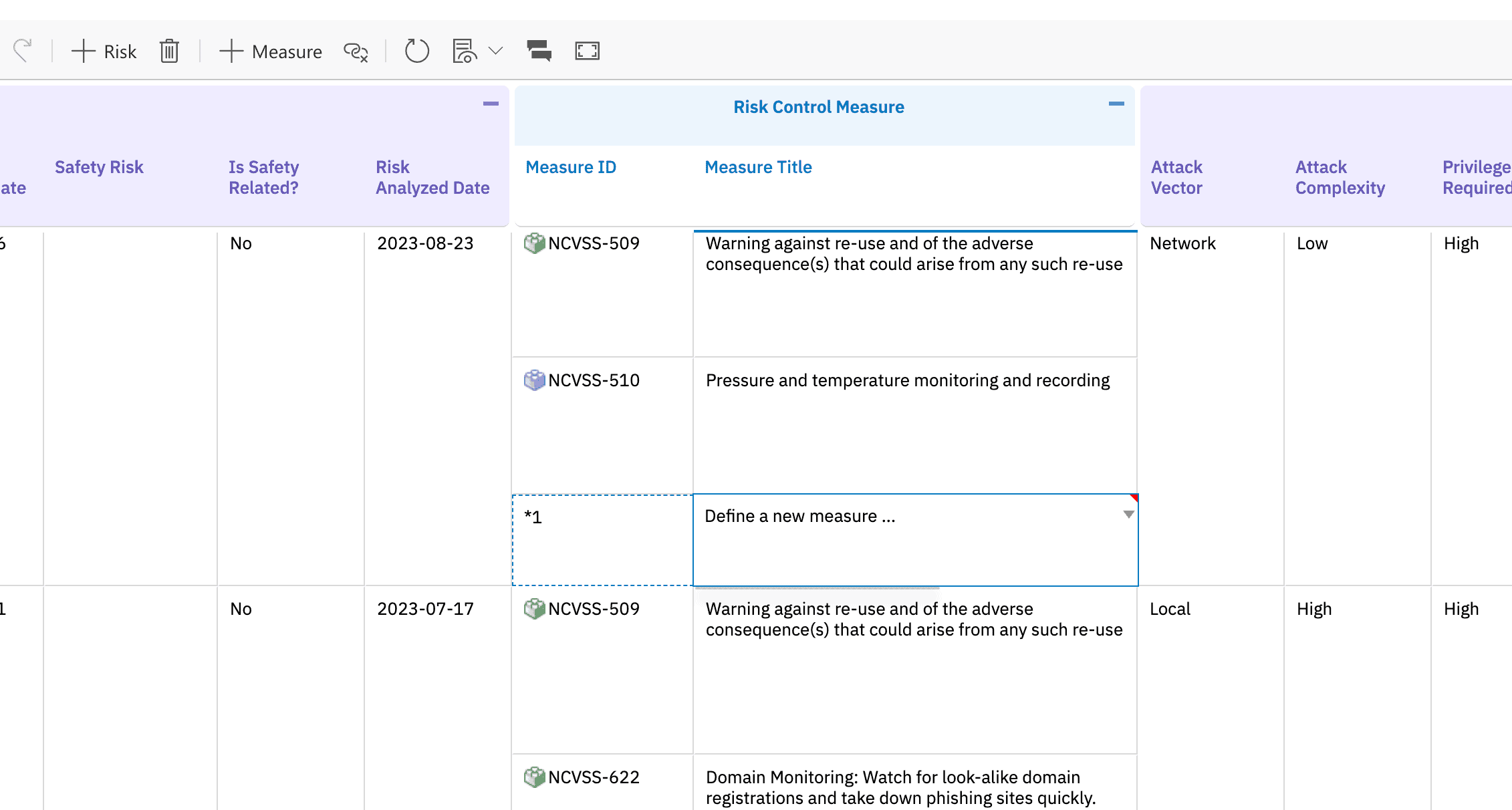
We provide the specialized capabilities essential for efficiently conducting TARA, managing vulnerabilities with CVSS, applying threat modeling like STRIDE, and ensuring compliance with standards such as IEC 62443 and ISO/SAE 21434.
Nextedy RISKSHEET is deeply embedded within Polarion ALM. Threats, vulnerabilities, assets, security goals, and controls are native Polarion Work Items, seamlessly connected to your system architecture, requirements, and test evidence.
- Eliminate disconnected threat logs and vulnerability spreadsheets.
- Foster collaboration between cybersecurity, development, and QA teams in one environment.
- Drive security by design by linking TARA findings to concrete security requirements.
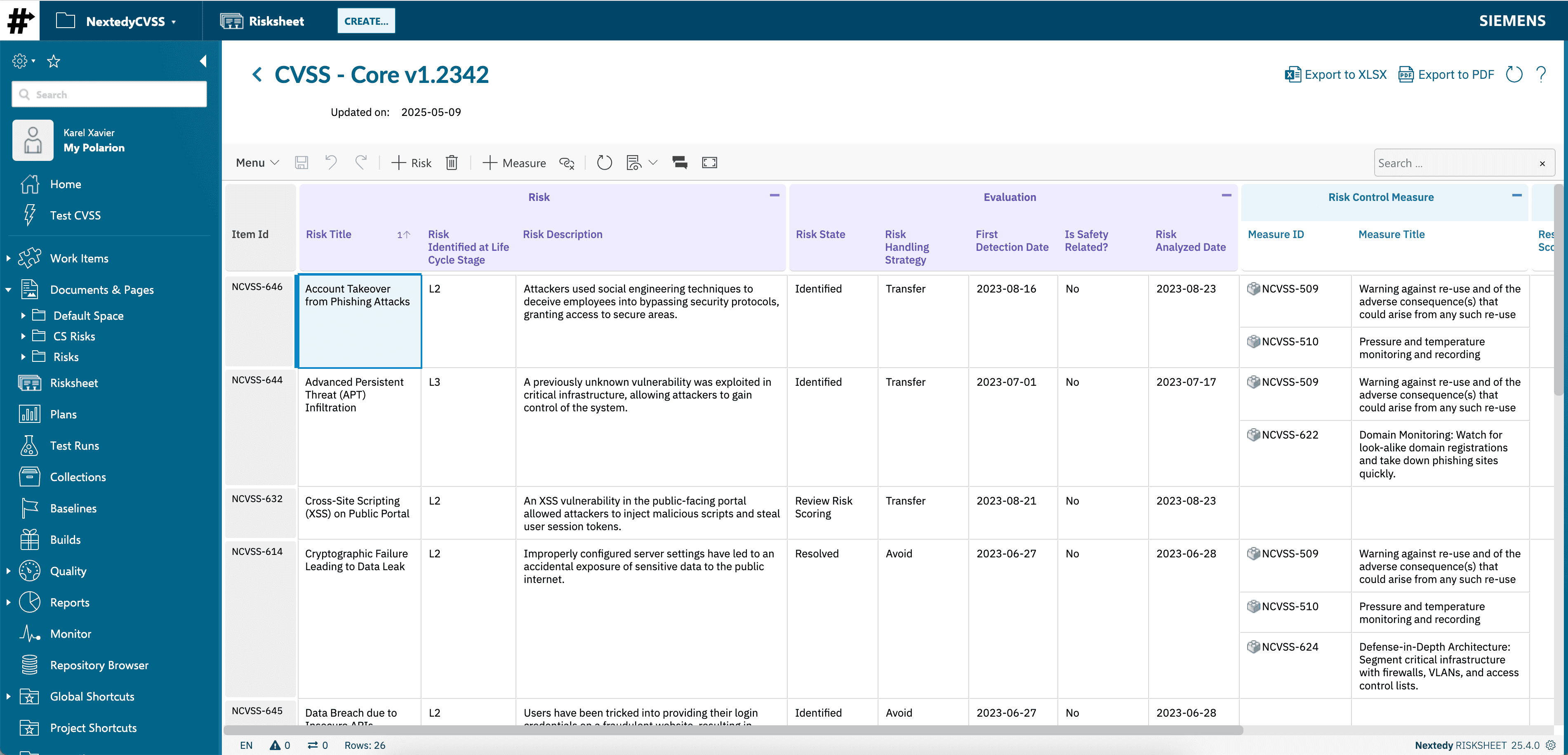
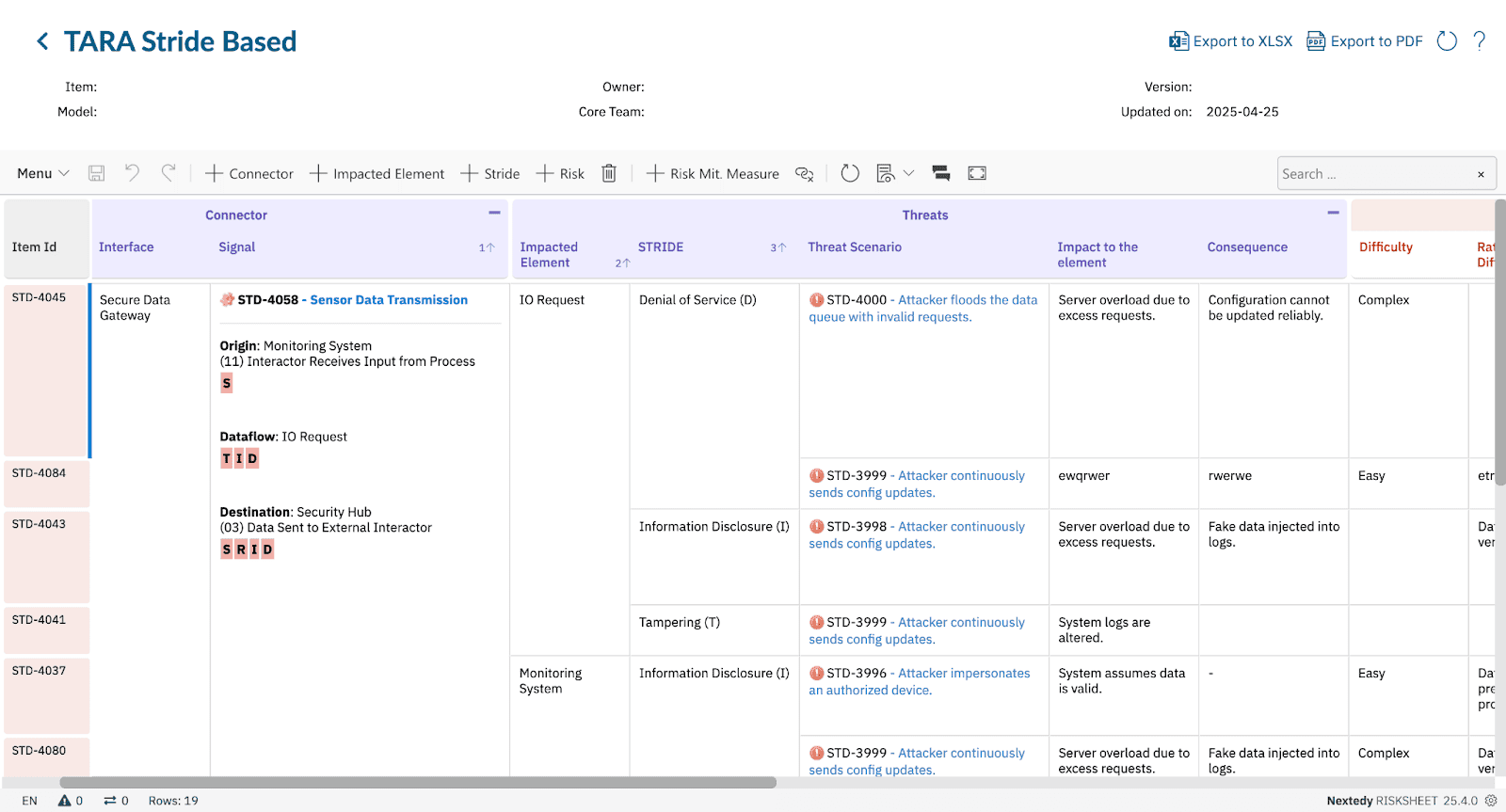
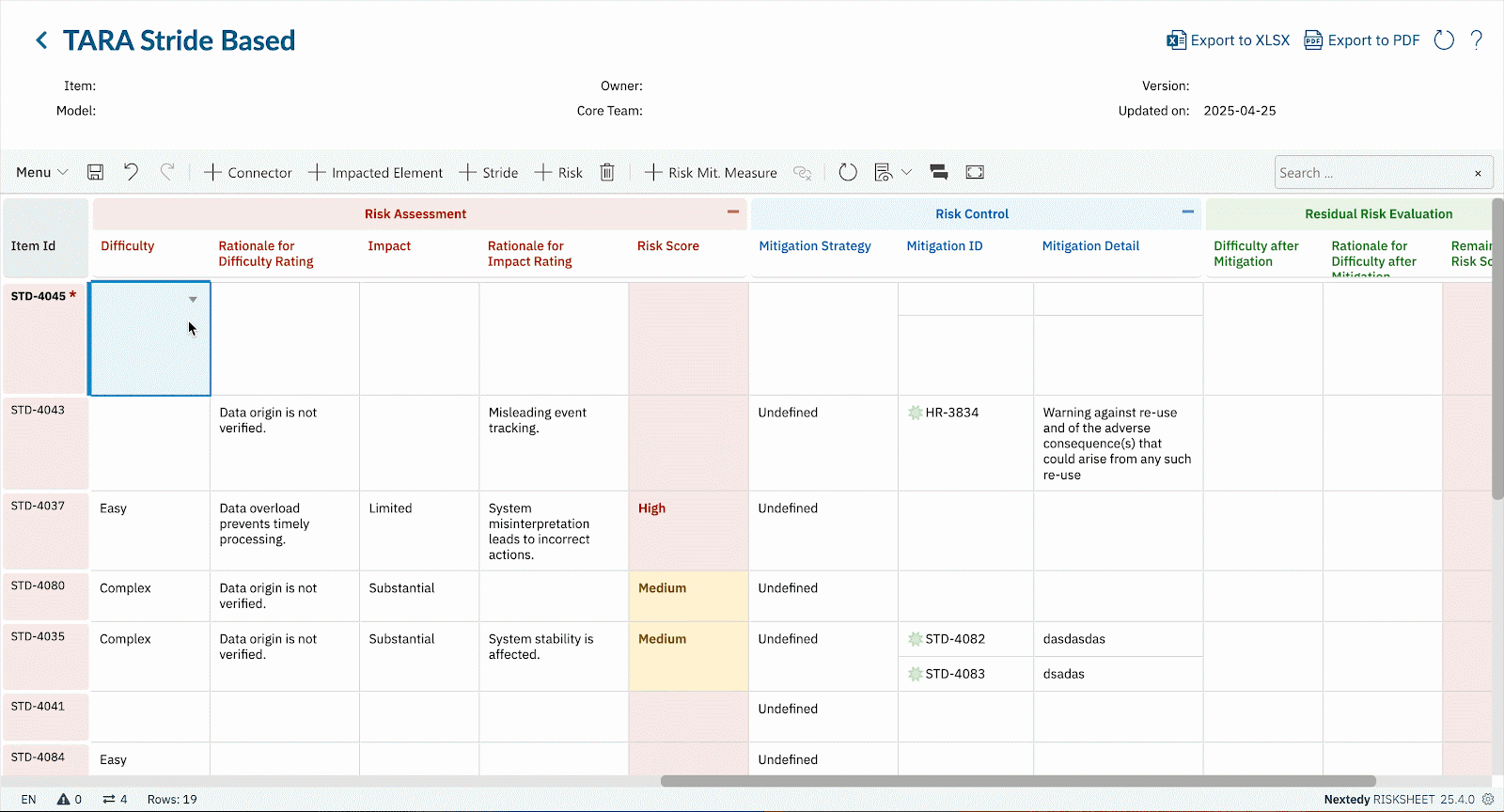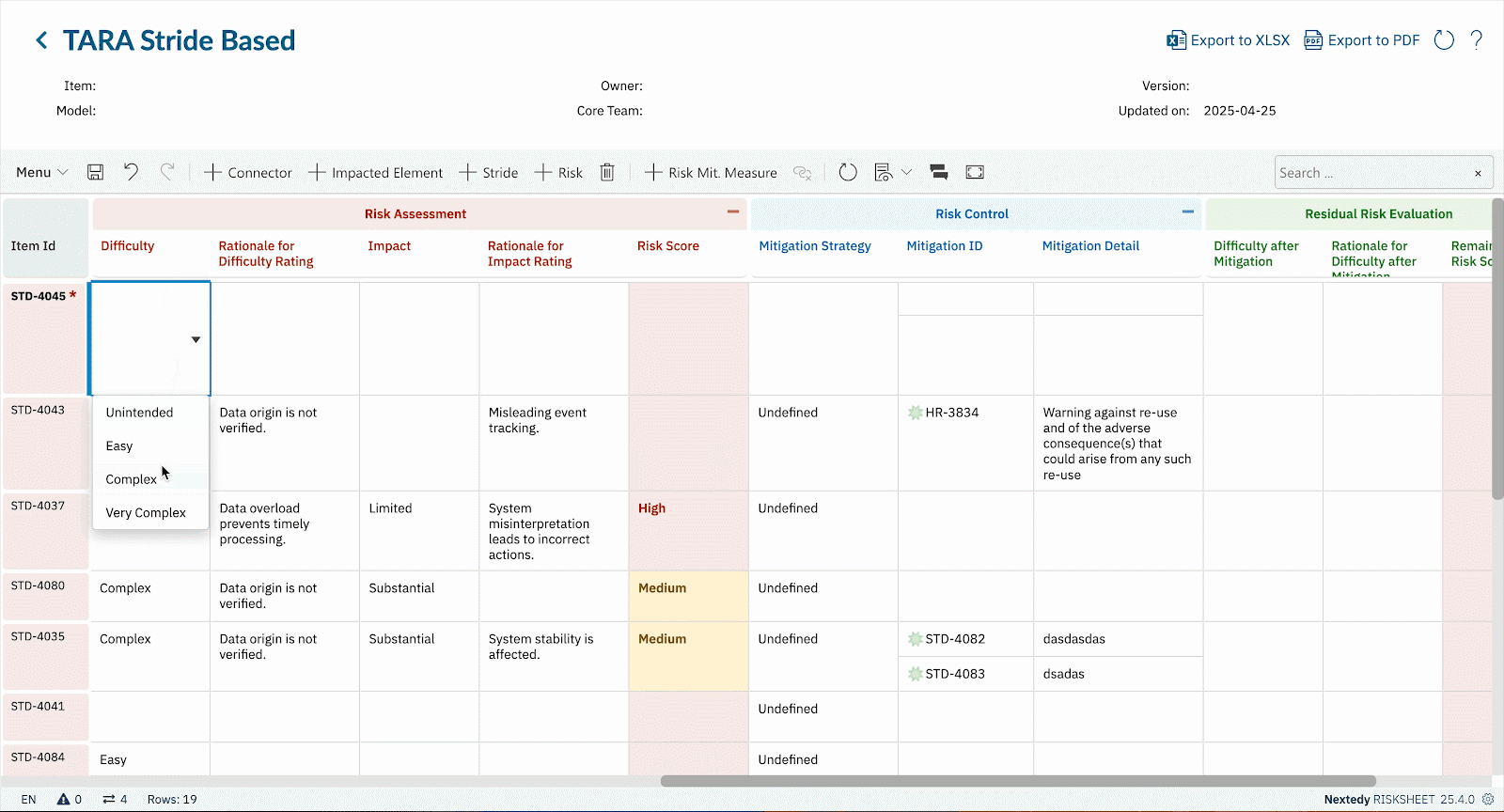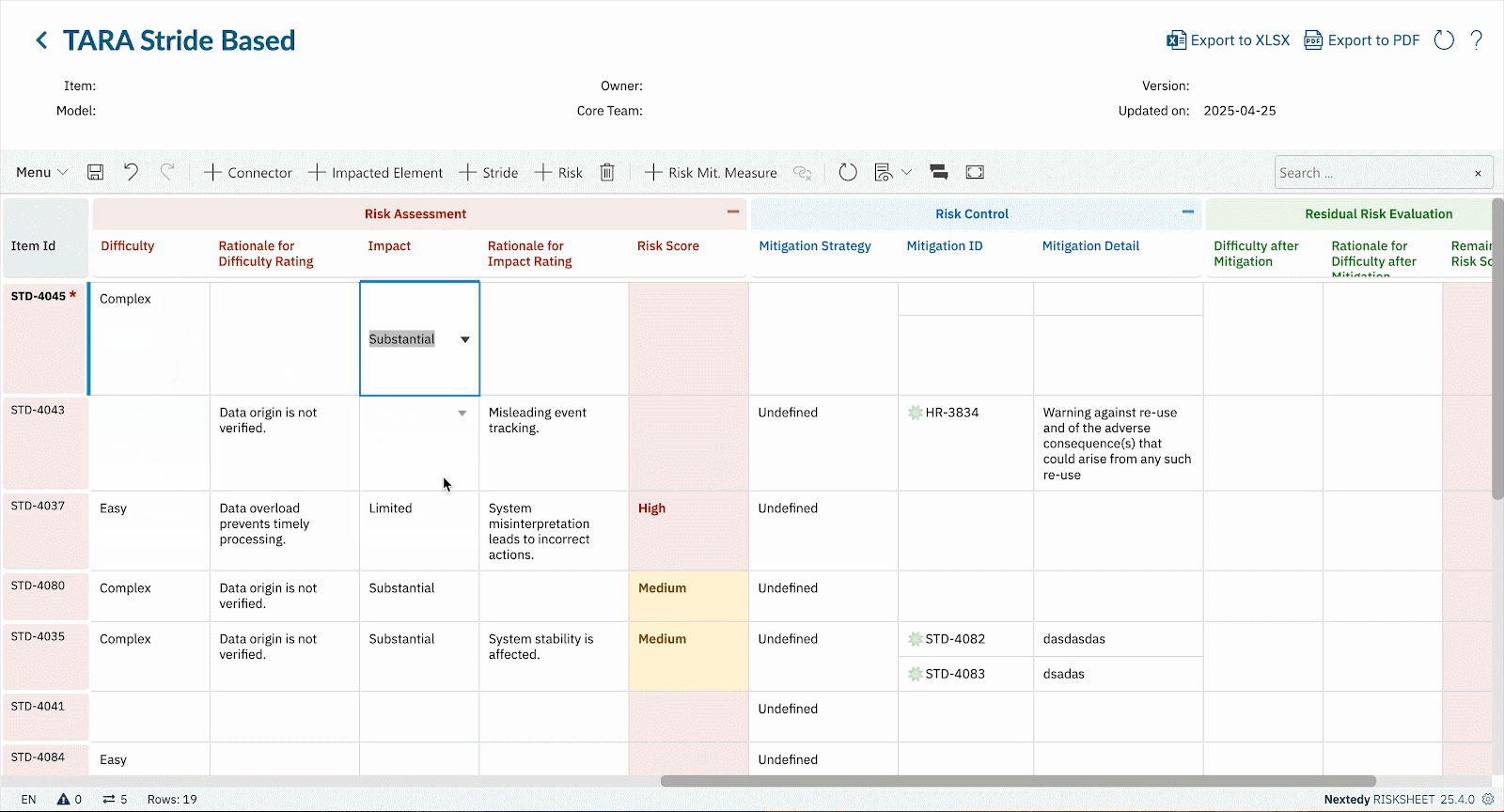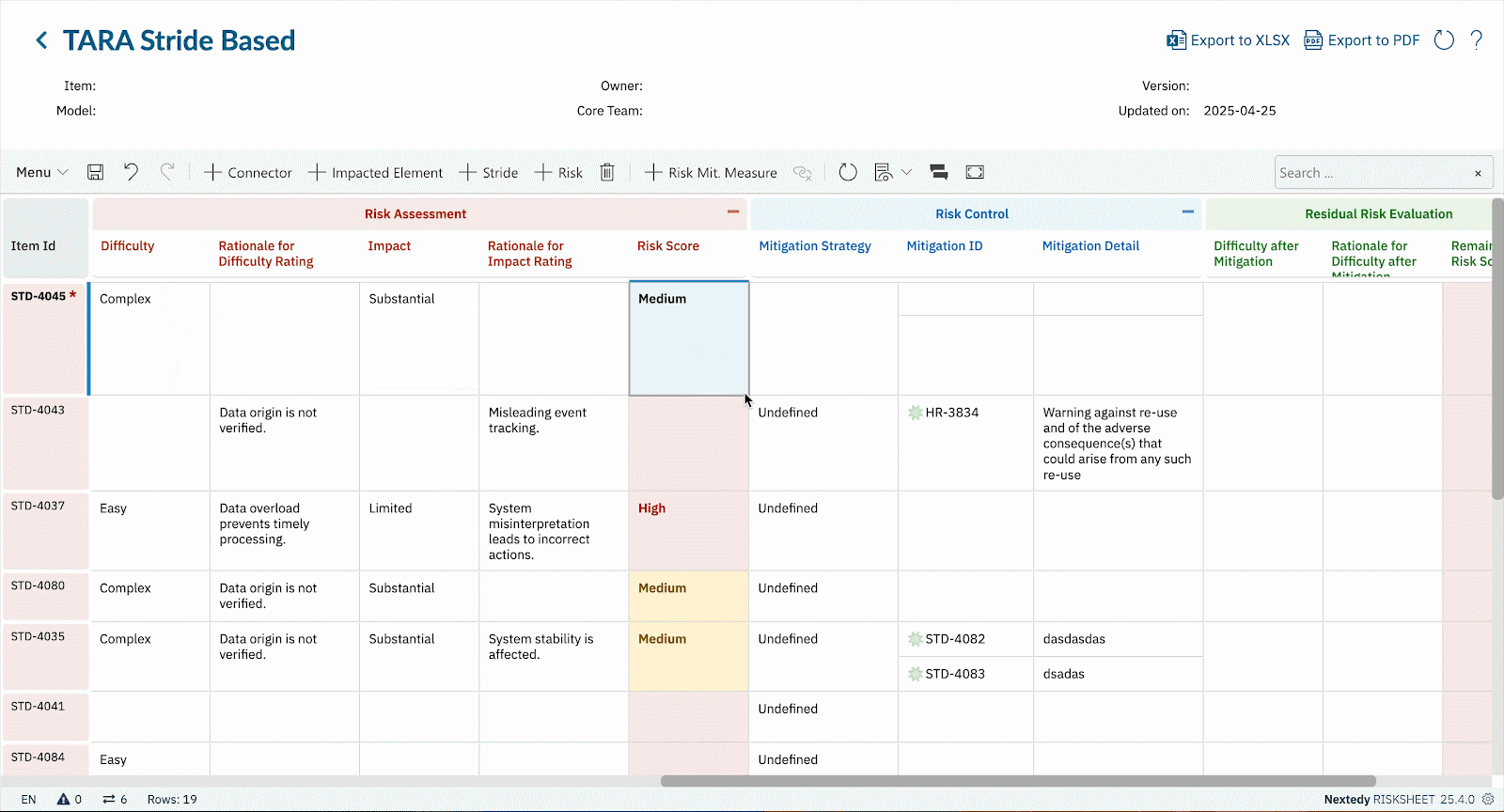
Boost productivity with RISKSHEET’s familiar spreadsheet-style layout for your TARA, CVSS scoring, or STRIDE threat modeling activities directly within Polarion LiveDocs.
Whether you’re conducting TARA per ISO 21434, assessing vulnerabilities using CVSS v3.1/v4.0, applying STRIDE for threat modeling, or adhering to IEC 62443 security levels, RISKSHEET offers fully customizable templates.
- Utilize our best-practice templates for common cybersecurity risk assessments or configure RISKSHEET to precisely match your methodologies and regulatory frameworks.
Ensure consistent application of threat assessment criteria, CVSS metrics, and security control definitions across your organization.
Integrate your cybersecurity risk management processes with Polarion’s workflow engine, enhanced by RISKSHEET:
Understand the lifecycle of your cybersecurity risks. Nextedy RISKSHEET leverages Polarion’s versioning for complete insight:
- Track every revision to TARA entries, CVSS scores, or identified threats.
- Formally baseline your cybersecurity risk assessments at key project gates.
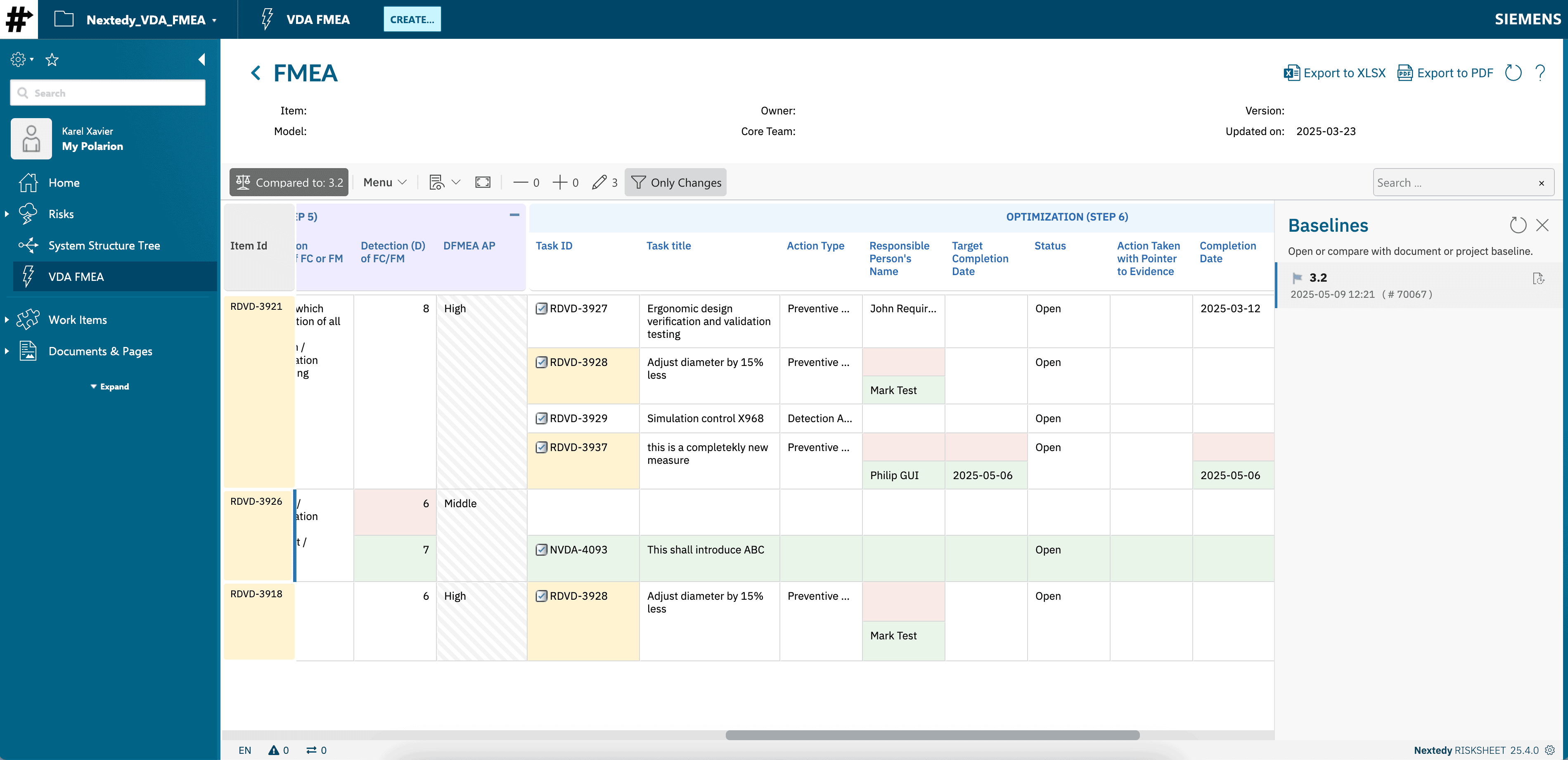
- Visually compare different versions or baselines directly within RISKSHEET. Identify changes in threat ratings, vulnerability scores, or security control effectiveness – vital for continuous monitoring and incident response planning.
Produce the necessary documentation for cybersecurity audits, type approvals, and internal reporting with confidence.
- Export comprehensive TARA reports, CVSS vulnerability lists, STRIDE threat summaries, and detailed audit trails directly from RISKSHEET (e.g., to Excel, PDF).
- Ensure documentation is always accurate, reflecting the live cybersecurity risk data within Polarion.
Built for Product Cybersecurity Leaders and Practitioners:
- Cybersecurity Managers & Engineers
- Product Security Officers (PSO)
- Threat Analysts & Vulnerability Management Teams
- Quality Assurance & Compliance for Secure Products
- System Architects focusing on Secure Design
See Nextedy RISKSHEET in Action:
Full Webinar On-Demand
- Discover how Nextedy RISKSHEET streamlines HARA (ISO 14971, ISO 26262) and FMEA (AIAG & VDA, IEC 60812) processes natively inside Polarion.
- See how to transform Excel-based safety analyses into dynamic, traceable, and auditable models.
- Learn to effectively link hazards, failure modes, safety goals, risk controls, and safety requirements.
- Understand how to maintain continuous compliance with key functional safety standards.
Evaluate RISKSHEET With a Real Project
Quick and easy way to validate the fit of cybersecurity management discipline integrated into Polarion ALM.
Set Up Your Proof of Concept – With Your Sample Data
- Validate the fit of Nextedy RISKSHEET while using your actual templates
- Collaborate with our team to tailor templates and workflows
- Experience full traceability, compliance, and user flow inside Polarion
- Start small. Scale when you’re ready.
Please, let us know your name and we get in touch to setup a Proof of Concept environment.

Convert your Excel Template
We take your current Excel TARA, CVSS, or STRIDE Excel templates and convert them into Polarion data models.

Review & Iterate with our Team
Review and provide feedback. After we help you tailor workflows, templates, and interfaces.
Mature your workflow at your pace
Any time, even after the initial rollout, implement catalogs, reusable assets, and model-based approaches.