In safety-critical industries, cybersecurity and functional safety can no longer be separated. Threats to connected vehicles, medical devices, and industrial systems are not just IT issues — they directly impact safety, compliance, and trust.
That’s why standards like ISO/SAE 21434 mandate structured Threat Analysis and Risk Assessment (TARA), linked to system requirements and mitigations. Yet, many organizations still perform TARA in spreadsheets or siloed tools, leaving it disconnected from the rest of the engineering process.
📌 What is TARA?
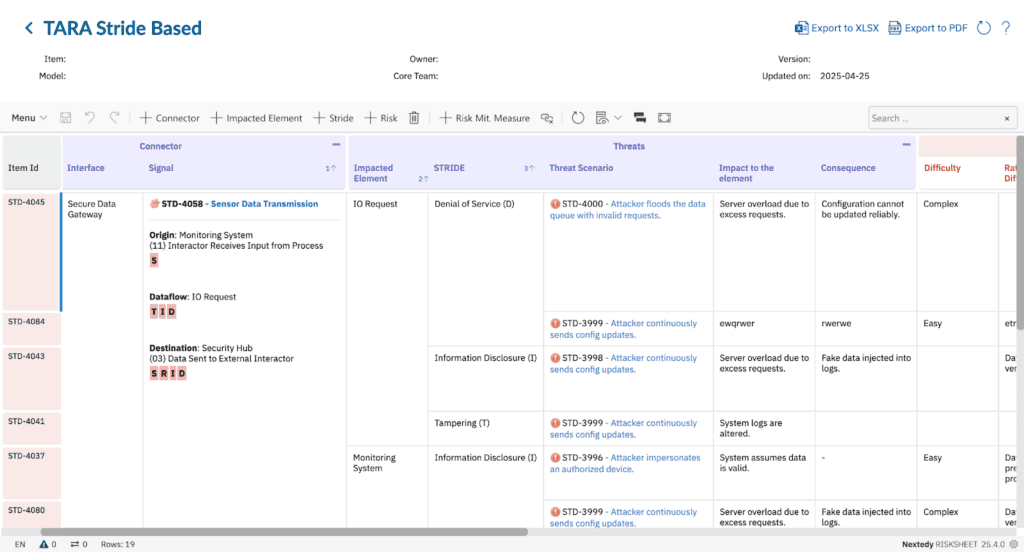
TARA (Threat Analysis and Risk Assessment) is a structured process defined in ISO/SAE 21434 for identifying cybersecurity threats to a system, estimating their impact and likelihood, and defining appropriate mitigations.
In simple terms, TARA helps organizations understand what could go wrong, how likely it is, and what must be done to protect the system. When performed inside Polarion with Nextedy RISKSHEET, TARA becomes traceable, auditable, and directly connected to your requirements, safety goals, and test cases.
As Nextedy states: “RISKSHEET transforms Siemens Polarion ALM into a dynamic, centralized hub for all your risk assessment activities.” Instead of treating cybersecurity risk management as an afterthought, RISKSHEET embeds TARA directly inside your requirements system — where it belongs.
Why TARA Must Live Alongside Requirements
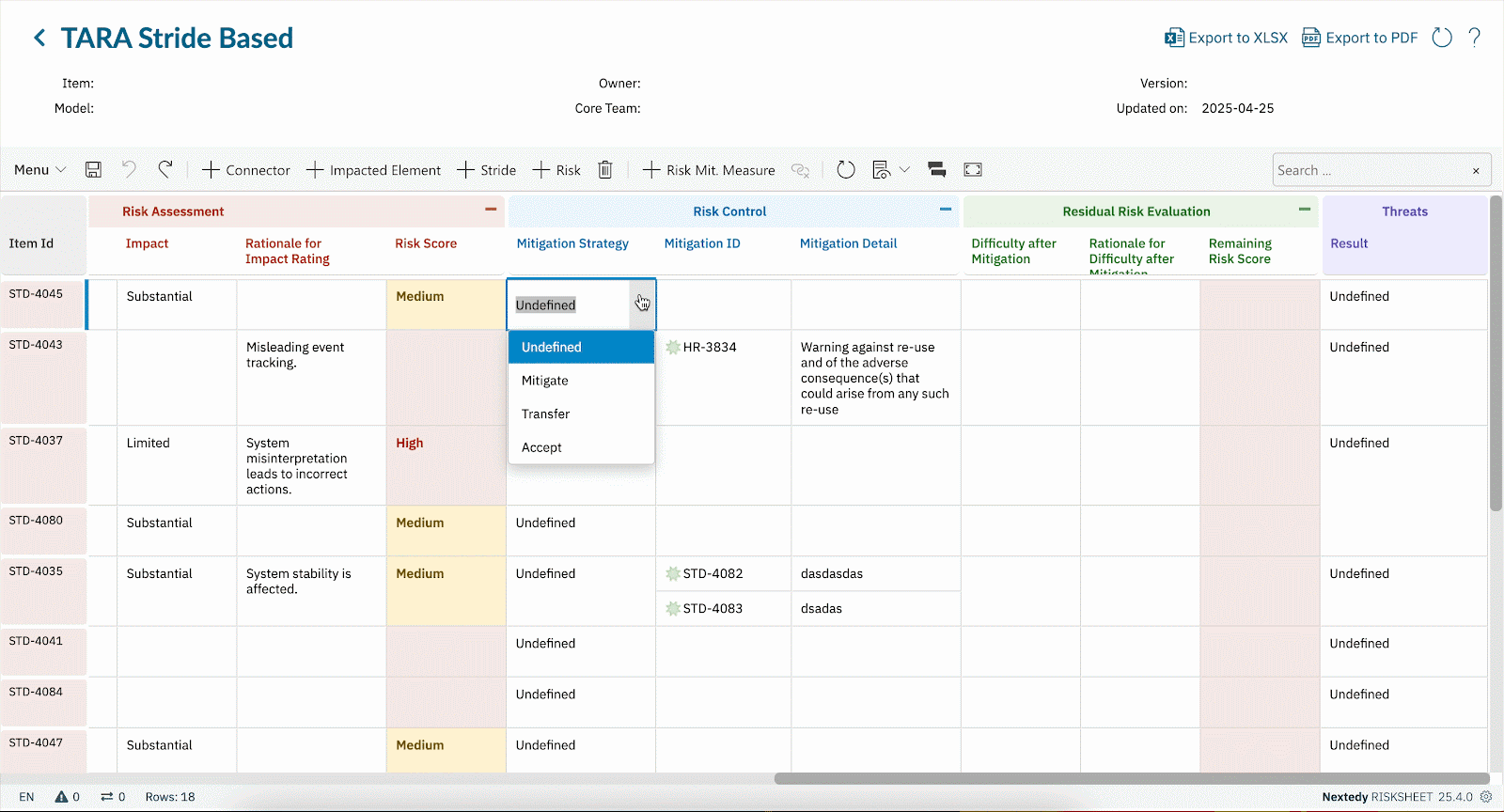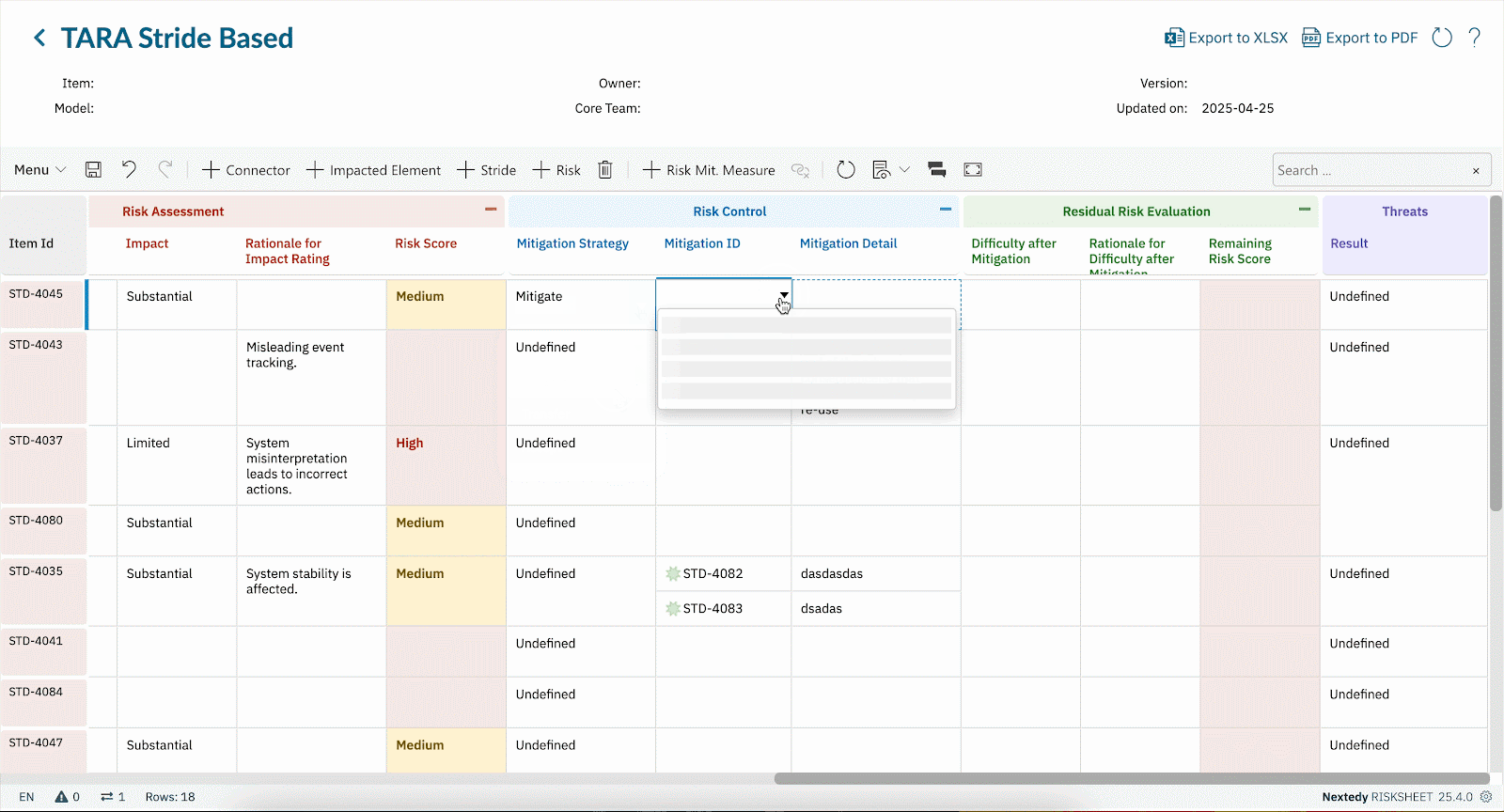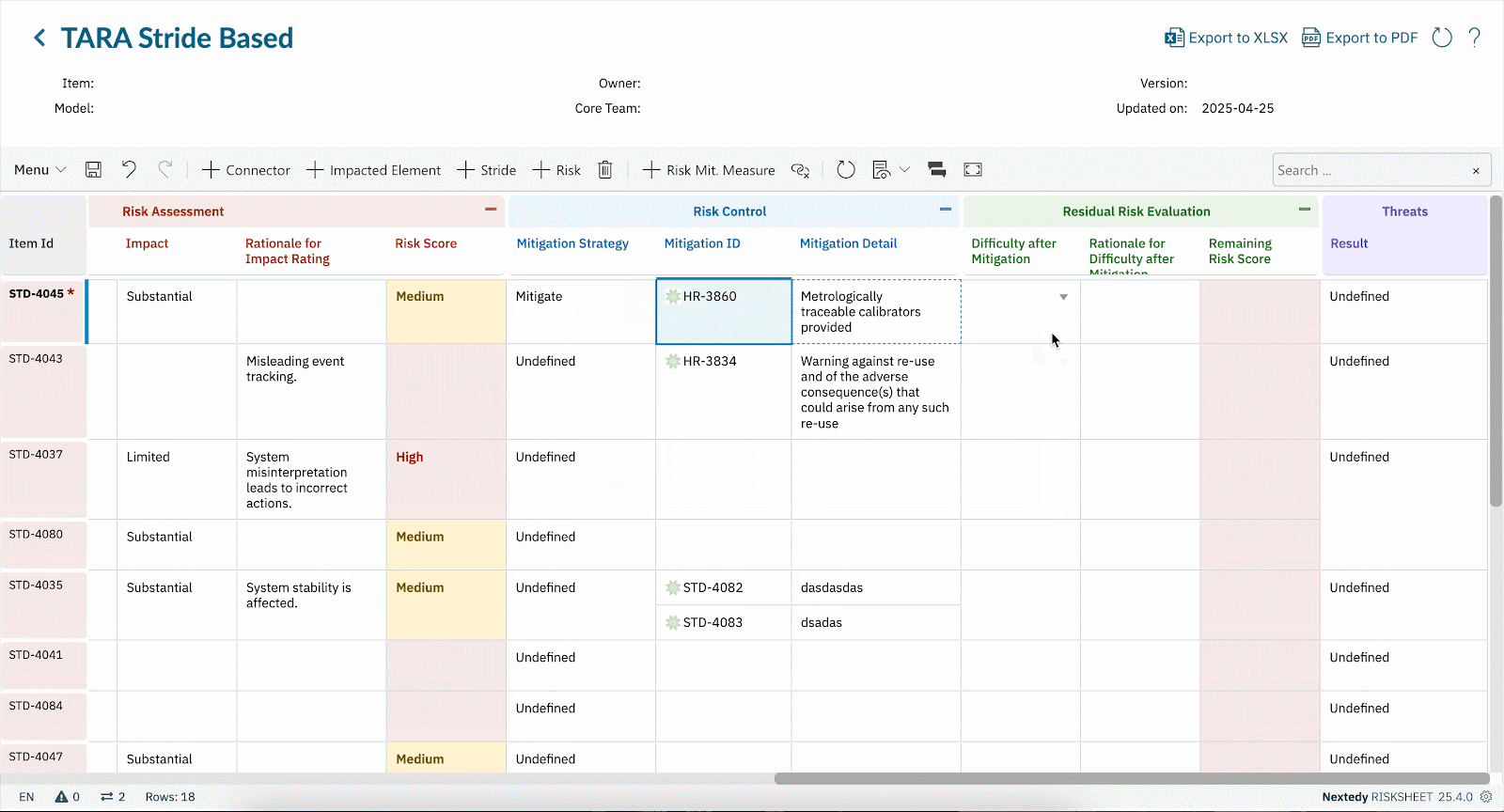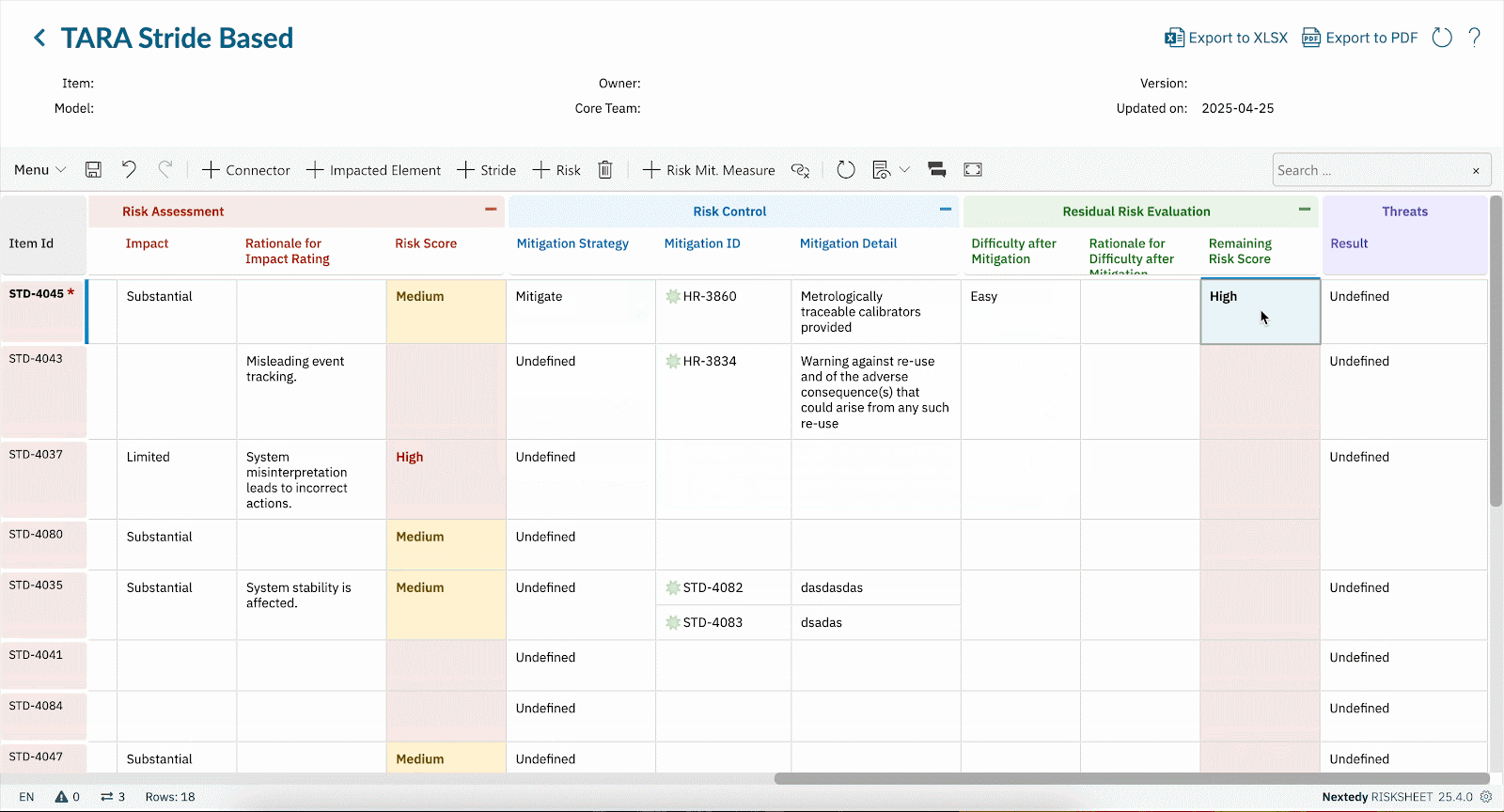
- Cybersecurity Risks Are Requirements Risks Every identified threat leads to requirements: secure communication protocols, hardened interfaces, authentication, monitoring. If TARA is in a spreadsheet, linking it back to requirements becomes manual, error-prone, and hard to audit. RISKSHEET makes this link seamless — each cybersecurity threat becomes a Polarion artifact, directly tied to the requirement it influences.
- Standards Demand Traceability ISO/SAE 21434 doesn’t just ask for a risk assessment — it requires traceability from threat to mitigation to verification. RISKSHEET ensures the TARA artifacts are fully embedded in Polarion, creating the evidence chain auditors expect.
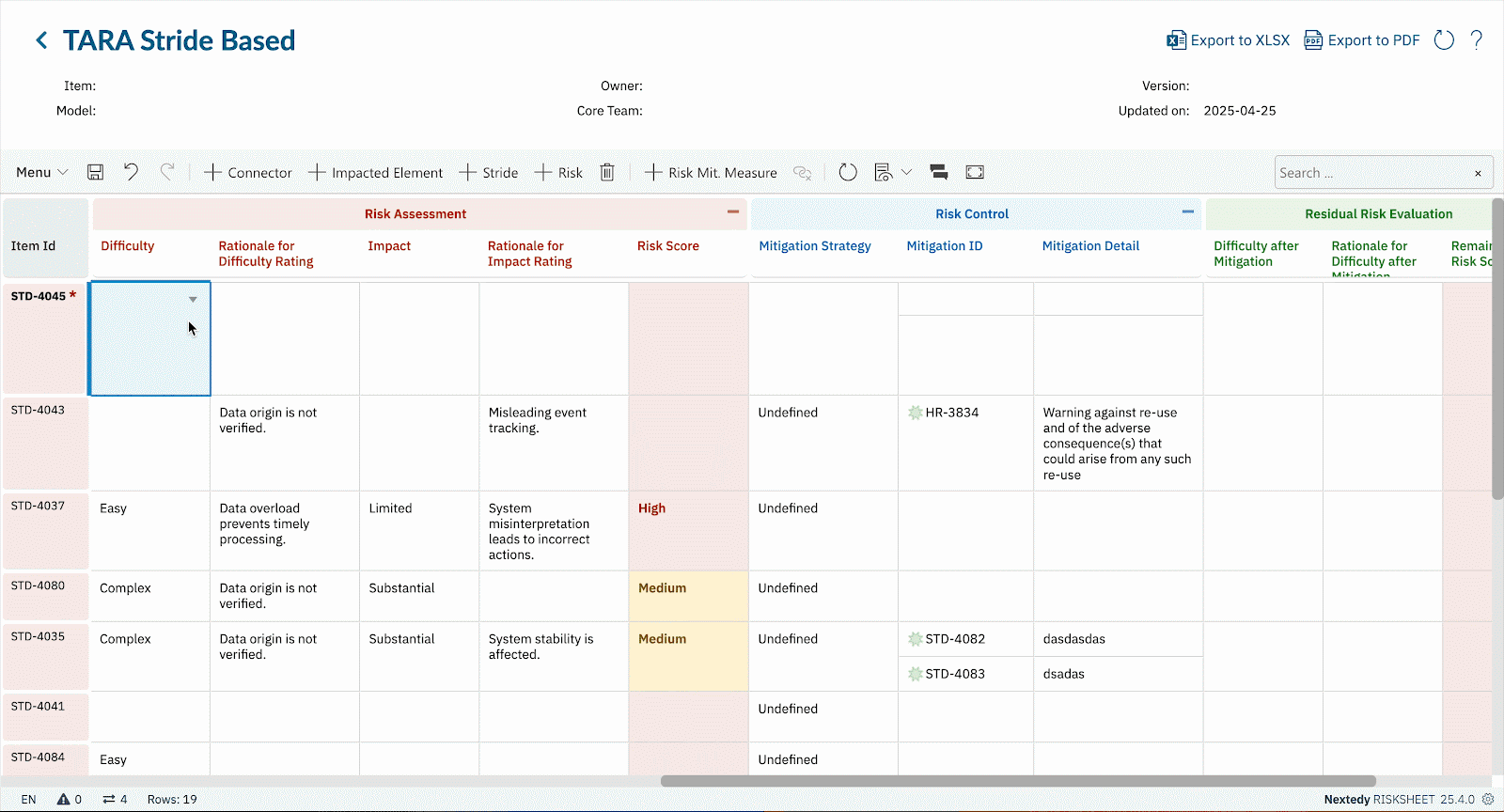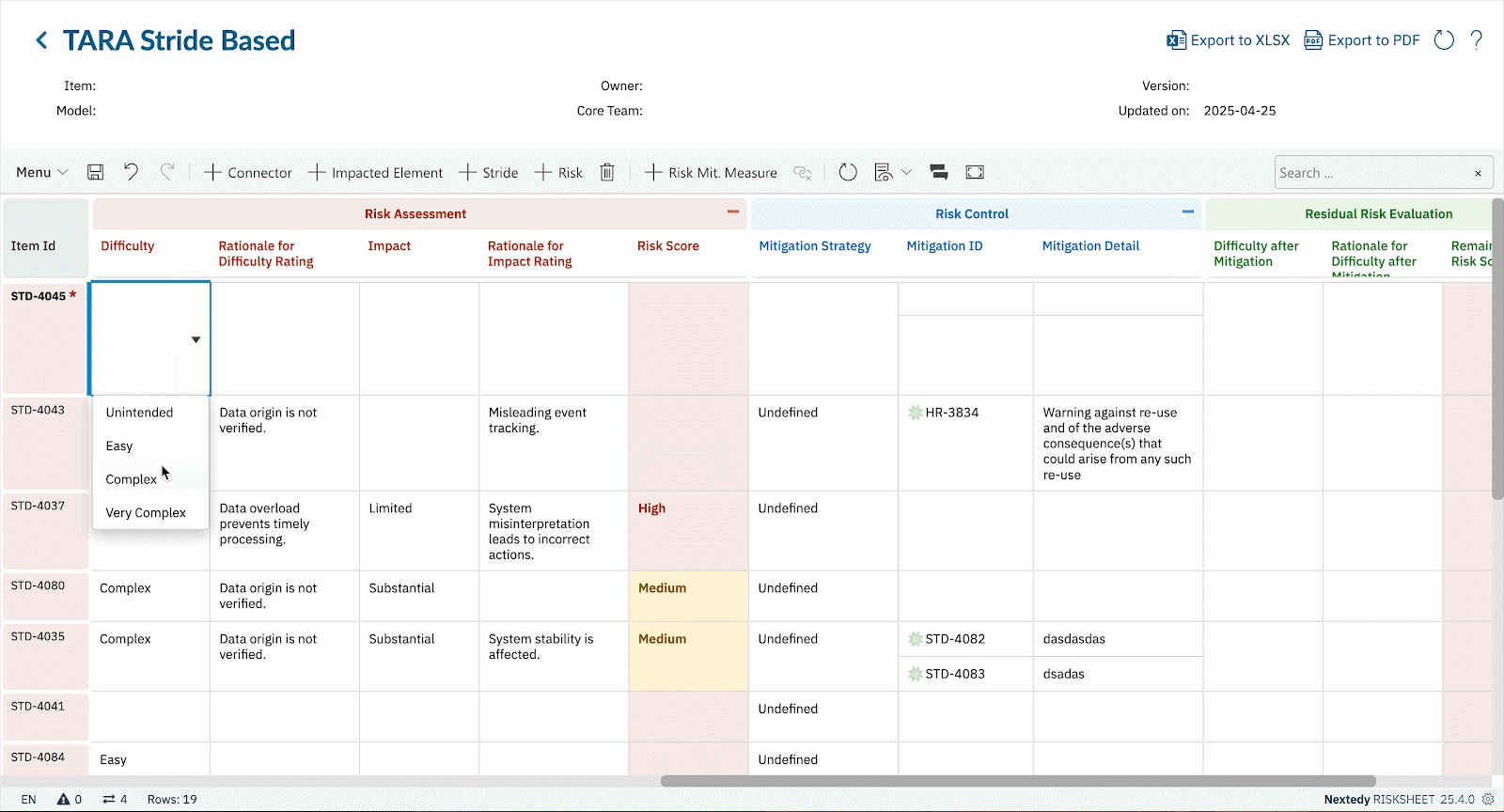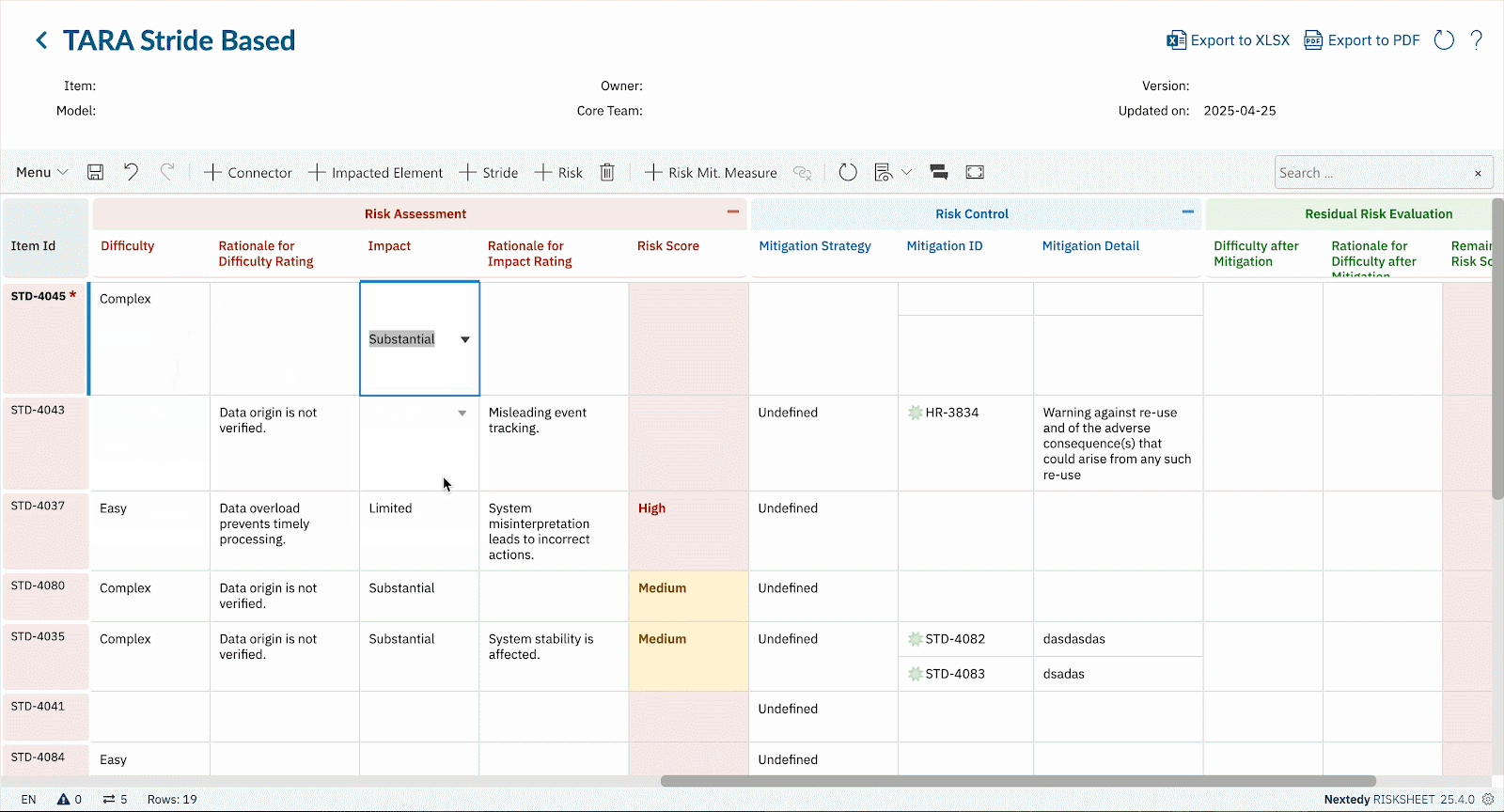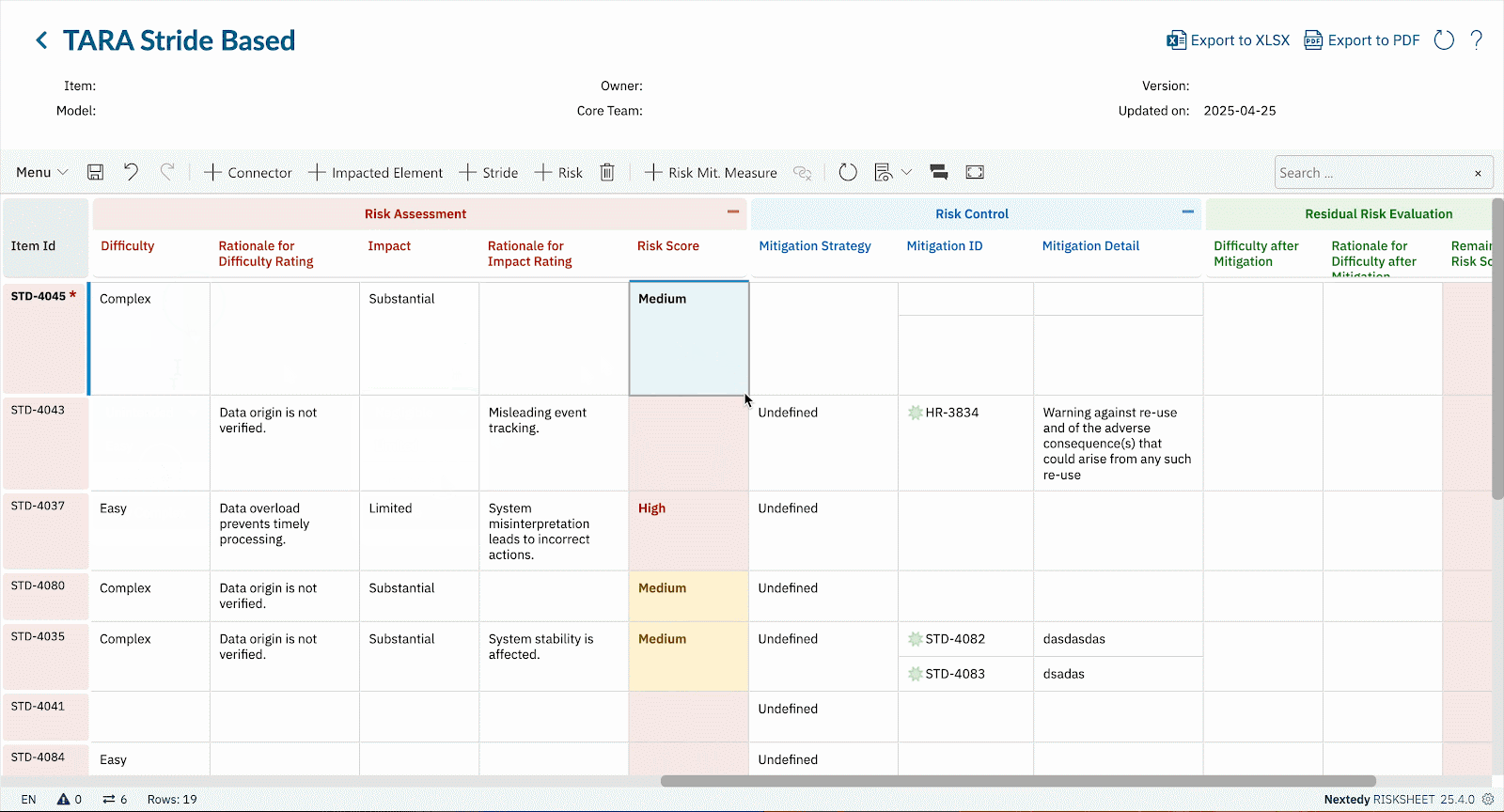
- Cybersecurity Is Not Static Threat landscapes evolve. What seemed acceptable risk yesterday may be unacceptable tomorrow. In RISKSHEET, updates in probability or severity automatically recalculate risk scores (e.g., CVSS). That means your TARA stays live, not frozen in an outdated spreadsheet.
- Collaboration Across Teams Cybersecurity cannot be left to a single role — it spans safety engineers, architects, testers, and compliance managers. RISKSHEET’s Excel-like interface inside Polarion allows all disciplines to work on the same data, without version chaos.
How RISKSHEET Brings TARA Into the Lifecycle
RISKSHEET is more than a table inside Polarion. It’s a cybersecurity-aware engine designed to align TARA with requirements, safety analysis, and testing:
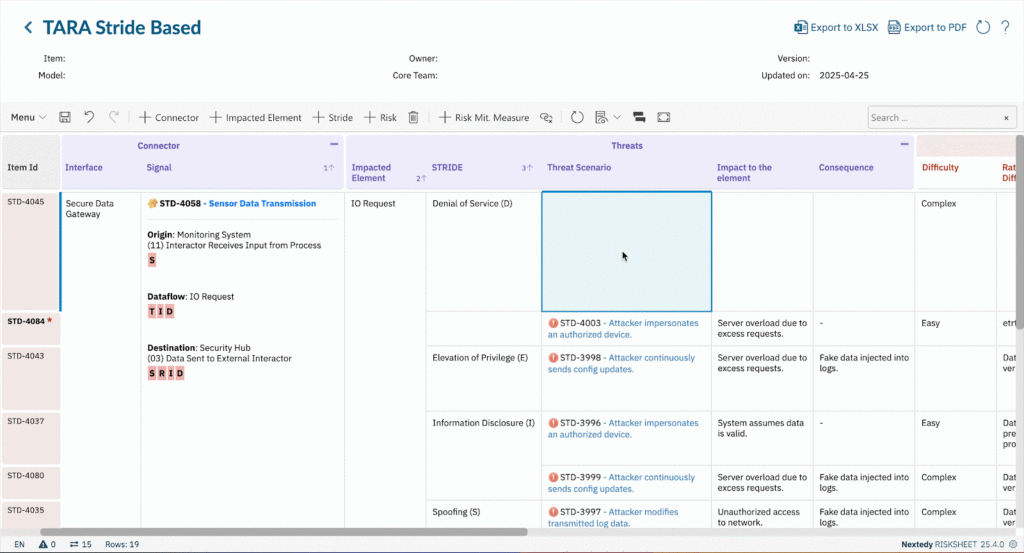
- TARA Methodology Inside Polarion Identify assets, threats, attack paths, and vulnerabilities. Calculate exposure, impact, and feasibility — all within Polarion.
- Link Threats to Safety & Requirements Map threats to safety goals, hazards, and system requirements. RISKSHEET ensures cybersecurity isn’t bolted on, but integrated with functional safety and system design.
- Automated Metrics & Formulas Use CVSS-style scoring or custom formulas to quantify risk consistently. As values change, RISKSHEET recalculates instantly.
- Full Traceability Chain From threat → requirement → mitigation → test case, RISKSHEET keeps the evidence trail unbroken, satisfying ISO/SAE 21434 and ISO 26262 simultaneously.
- Audit-Ready Outputs Export tailored PDF reports from RISKSHEET for compliance reviews — with baselines and compare mode to show revisions over time.
Unique Advantage: Aligning Cybersecurity With Functional Safety
Many organizations treat functional safety (ISO 26262, ISO 14971) and cybersecurity (ISO/SAE 21434, IEC 62443) separately. The real world doesn’t. A cyberattack on a braking system is both a safety and security issue.
RISKSHEET is uniquely positioned to align TARA with FMEA, HARA, and safety risk assessments. This gives organizations:
- One system of record for safety and security risks.
- Consistent methodologies across disciplines.
- Shared collaboration between cybersecurity and safety teams.
- Reduced audit burden, since evidence comes from the same Polarion database.
As we say at Nextedy: “Stop battling spreadsheets. RISKSHEET gives you an interactive, traceable, and compliant solution built to handle enterprise-level risk management.”
The Cybersecurity Payoff
By embedding TARA into Polarion with RISKSHEET, you gain:
- Compliance confidence: ISO/SAE 21434, IEC 62443, and functional safety standards.
- Continuous cybersecurity awareness: risks updated as requirements evolve.
- Full lifecycle integration: threats traced through requirements, design, and test.
- Audit-ready evidence: instant reporting and baselines.
👉 Nextedy RISKSHEET brings cybersecurity risk management out of isolated spreadsheets and into your ALM system, uniting TARA with requirements, safety, and compliance. Because in connected, safety-critical systems, security is safety.